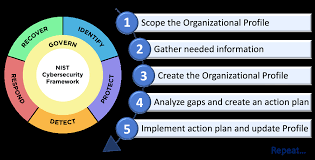
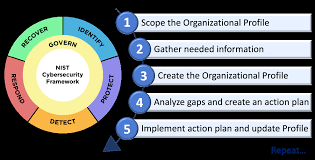
Improving the Performance of Technical Systems , Upholding the Productivity of a Company
ISU&I involve implementing technical controls like strong passwords and multi-factor authentication, regular software updates, and data backups, combined with a strong security culture through user training and clear policies on remote work and incident response. Continuous processes such as risk management, security assessments, and monitoring are also vital to maintaining a strong defense against evolving threats. Improving and upgrading information security requires a comprehensive, continuous, and multi-layered approach that combines technology, policies, and human awareness to protect sensitive information and systems.
Information Security Upgrades and Improvements
Technical and structural improvements
Strengthen access controls: Enforce strong, unique passwords and implement multi-factor authentication (MFA) to add an extra layer of security.
Keep software updated: Regularly patch and update all operating systems, applications, and security software to close known vulnerabilities.
Improve network security: Deploy firewalls and other network security tools to monitor and protect the network perimeter. Consider physically separating critical resources when possible.
Secure remote access: Require the use of VPNs and secure configurations for remote workers to protect data in transit.
Back up data: Regularly back up important data and store backups in a secure, separate location to enable recovery from incidents like ransomware attacks or hardware failure.
Configure devices securely: Ensure all connected devices, including mobile and portable ones, are properly configured and secured.
Policy and process improvements
Develop clear policies: Establish comprehensive policies for security, including those for password management, remote work, and incident response.
Implement the Principle of Least Privilege: Grant users only the minimum access necessary to perform their job functions to limit the potential damage from a compromised account.
Plan for incidents: Create and test an incident response plan so that the organization can react quickly and effectively to a security breach.
Human and cultural improvements
Prioritize user training: Educate employees on how to recognize and avoid threats like phishing emails and suspicious links. Training should be ongoing and practical, not just a one-time event.
Foster a culture of security awareness: Encourage everyone to take responsibility for security and to report suspicious activity without fear of reprisal.
Ongoing and strategic improvements
Conduct regular assessments: Perform risk assessments and vulnerability tests (like penetration testing) to identify weaknesses before they can be exploited.
Monitor systems: Implement logging and monitoring to track activity, detect anomalies, and respond to threats promptly.
Stay informed: Continuously review and update your security practices to stay ahead of new and evolving threats.
Align with business goals: Ensure security improvements are aligned with the organization's overall business objectives.
Key strategies for an effective information security upgrade and improvement program include:
1. Foundational Steps and Strategy
Conduct a Security Posture Assessment: Begin by evaluating your current policies, procedures, and security safeguards to identify existing gaps and risks. Third-party security audits and penetration testing can help spot vulnerabilities you might overlook.
Prioritize Risks: Focus on mitigating the most significant business risks first, such as protecting customer data or intellectual property. This makes the process more manageable than trying to address everything at once.
Develop an Incident Response Plan (IRP): Even with robust security, breaches can happen. A formal IRP outlines the roles, responsibilities, and steps to minimize impact and ensure a quick recovery in case of an attack.
Define Clear Policies: Create and communicate comprehensive cybersecurity policies covering password management, data access, incident reporting, and remote work guidelines to guide employee actions.
2. Technical Implementations
Regular Software Updates and Patch Management: Unpatched software is a primary entry point for attackers. Automate software updates for operating systems, applications, and security programs to ensure all systems have the latest security patches.
Implement Strong Access Controls:
Multi-Factor Authentication (MFA): Enforce MFA for all user and administrative accounts to add an essential layer of security beyond passwords.
Principle of Least Privilege: Limit user access to only the data and systems necessary to perform their jobs.
Strict Password Policies: Mandate the use of complex, unique passwords (over 10 characters with a mix of letters, numbers, and symbols) and consider using a password manager to help employees manage them.
Deploy and Configure Security Tools: Use firewalls and intrusion detection systems to monitor network traffic and block unauthorized access. Ensure endpoints (computers, smartphones, tablets) have up-to-date endpoint protection software.
Encrypt Data: Encrypt sensitive data both at rest (stored on devices or in the cloud) and in transit (during transmission) to protect it from unauthorized access, even if systems are compromised.
Secure Network Connections: Mandate the use of Virtual Private Networks (VPNs) for all remote work to encrypt network traffic, especially when using insecure public Wi-Fi networks.
Back Up Data Regularly: Store encrypted backups of critical data in a secure, separate location (e.g., the cloud or an external hard drive stored offline) to ensure recovery from ransomware attacks, accidental deletion, or hardware failure.
3. Human Factor and Culture
Prioritize Staff Training: Most security breaches are due to human error. Conduct regular, engaging training sessions to educate employees about phishing scams, safe browsing, social media risks, and proper data handling procedures.
Foster a Security-Aware Culture: Make security a core part of the company's values so that all employees understand their role and responsibility in protecting information assets.
Manage Insider Threats: Implement systems to monitor network traffic for suspicious behavior or unusual data access requests by internal personnel (both malicious and unintentional).
4. Continuous Improvement
Information security is an ongoing, iterative process, not a one-time fix. The Plan-Do-Check-Act (PDCA) cycle or similar frameworks provide a structured approach to:
Plan: Identify new opportunities for improvement.
Do: Implement the changes.
Check: Monitor and evaluate the results of the changes.
Act: Adjust the plan based on the feedback and implement successful changes on a larger scale.
By integrating these practices and staying informed about the latest threats and technologies, organizations can significantly enhance their security posture and resilience against cyber threats.